
This level of anonymity makes the dark web a haven for illegal activities, such as drug trafficking and various types of cybercrime. The dark web is a subset of the deep web, which includes any online content not visible on normal search engines, such as private databases and personal email accounts. It operates on a separate network that anonymizes users by routing their traffic through a series of encrypted servers, making it difficult to trace activities or identify users. It’s a hidden layer of the internet, shrouded in secrecy, that you can’t access using traditional search engines like Google or Bing. It’s often used for anonymity, both for legitimate privacy reasons and for illegal activities like black market trading or data leaks.

Privacy Precautions Before Accessing The Dark Web On Your Phone
Also, try its services risk-free with the 30-day money-back guarantee. If the VPN connection fails, the automatic kill switch will kick in, temporarily breaking your traffic. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption. All the plans come with a 30-day money-back guarantee, so you can try the services risk-free.
Is The Tor Browser Safe Without A VPN?

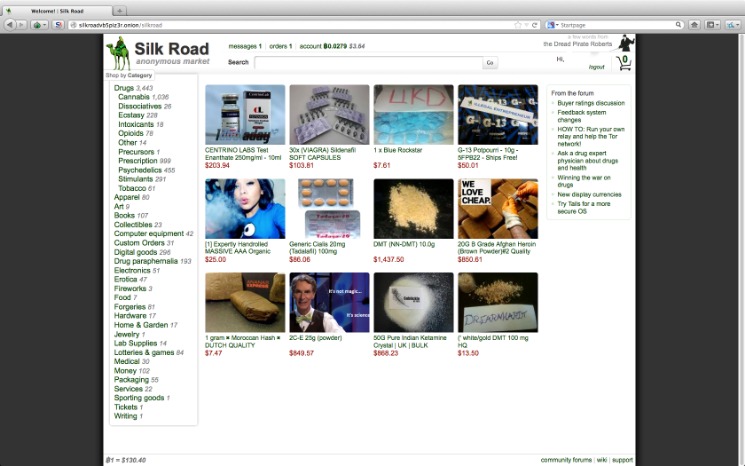
The dark web can certainly be dangerous — with no regulation, it’s a riskier place to hang out than the surface web. The dark net is not quite as lucrative as it used to be and the prices for most of these items or services have gone down in recent years. Here’s a look at several of the illegal items you can buy — with prices — courtesy of Privacy Affairs’s Dark Web Price Index 2023.
Why Do The Darknet And Deep Web Exist? Legitimate Uses
You can use a VPN if you’re in a country that restricts or heavily monitors Tor usage. Whenever you enter any domain into the address bar, your browser uses HTTP to find and request the data from the relevant server. A little typo can lead you to a clone designed to trick users into handing over sensitive data. Onion sites end in “.onion” instead of “.com,” “.co,” “.net,” etc. Many popular websites, such as Facebook and DuckDuckGo, have Onion versions, so check if yours has one. The tradeoff is that you don’t get personalized search results, as DuckDuckGo doesn’t collect user data.
Choose A Dark Web Search Engine

Access to ".onion" domains and anonymous surfing made possible by specialised software like the Tor Browser allows entry only. People often have bad feelings about the dark web, but not everything on it is illegal or dangerous. Install Avast SecureLine VPN for iOS to protect your privacy and keep your data from falling into the wrong hands.
- Doing so can tie your activity back to you, destroying your anonymity.
- Again, it’s DOT Security’s advice to stay off the dark web entirely.
- For example, you can find information unavailable to the public and share data privately while protecting your online identity.
- What is a firewall, and why is it your first line of defense in network security?
Another advantage of I2P is that it uses one-way tunnels so that an eavesdropper can only capture inbound or outbound traffic but not both. I2P does not depend on a trusted directory to get route information. Among its users are oppressed people, journalists, and whistleblowers as well as the average person looking to secure his privacy.
Stan has over 7 years of cybersecurity experience, holding senior positions in information security at General Motors, AIG, and Aramark over his career. In short, even with Tor, there's no perfect anonymity online, but there are efforts to claw back our power online, says Lewis. "The big win of Tor for me is access — with a sprinkling of anonymity, to be sure — but that I can be stuck behind some hotel firewall, in some airport or restaurant lounge, or in a sketchy cafe is a sketchy country," Muffett says. To review security settings, click on the onion logo in the top left and select "Security Settings", which will bring up a slider offering a choice of the default of standard, or safer and safest. The latter choice is for when access to the Tor network is blocked, and you'll be shown a variety of circumvention techniques.
It has onion links you cannot access with regular browsers like Chrome, Firefox, Edge, or Safari. This article lists some of the best dark web websites you can visit securely. Well, as long as you don't visit sites with underaged models or that engage in human tracking or that sell drugs and other illegal items. Tor Browser has since become a popular tool of journalists, activists, and others that may be subject to being monitored online. Tor was developed in the mid-1990s by United States Naval Research Laboratory employees, mathematician Paul Syverson, and computer scientists Michael G. Reed and David Goldschlag.
The Hidden Wiki and its mirrors and forks hold some of the largest directories of content at any given time. Specialist Clearweb news sites such as DeepDotWeb and All Things Vice provide news coverage and practical information about dark web sites and services; however, DeepDotWeb was shut down by authorities in 2019. Media coverage typically reports on the dark web in two ways; detailing the power and freedom of speech the dark web allows people to express, or more commonly reaffirms the illegality and fear of its contents, such as computer hackers. Many journalists, alternative news organizations, educators, and researchers are influential in their writing and speaking of the dark web, and making its use clear to the general public.
Is It Illegal To Visit The Dark Web?
Naval Research Lab as a system of decentralized, anonymous nodes to enable anonymous online communication. When accessing the dark web, the first step is to install a dark web-friendly browser on your computer. Legitimate content on the dark web includes freely accessible news from independent or international sources, and forums and communities centered around niche interests. Another difference you’ll notice is that instead of seeing web addresses with a “.com,” “.org,” “.edu,” or “.gov” suffix, they’ll end in “.onion.” In most ways, the dark web resembles the clear web, but dark web sites often have a text-heavy, minimalistic design focused on anonymity and functionality. The dark web is a small, hidden subset of the deep web that requires special tools to access.
Best Dark Web News Sites Offering Factual Information

Due to all the nodes that your traffic passes through, Tor by itself significantly limits bandwidth. Some consider VPN over Tor more secure because it maintains anonymity throughout the entire process (assuming you pay for your VPN anonymously). The VPN over Tor technique is also susceptible to an end-to-end timing attack, though it’s highly unlikely. This means the VPN provider doesn’t see your real IP address and the VPN protects you from those bad exit nodes.
You should only ever access websites you know are safe because they're vetted by websites or other sources that you already know are safe. But be warned, it's not as user-friendly as the typical clearnet websites you access. It uses the onion router to bounce your signal around other Tor users around the world, thereby pseudo-anonymizing you when you access the dark web. There are many legitimate websites on the dark web that can be worth visiting, but there are also the absolute extremes of illegal material, such as pornography, illegal substances, and gore.
Scams And Fake Marketplaces
If you want to find its current links, you can search for terms like “Daniel replacement.” Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). Hence, you never know when a popular .onion site is going to vanish, or even die.
You can change the IP address the Tor network assigned to you by connecting to different servers — to do that, first click the padlock icon next to the site’s URL bar. If you want to surf .onion sites, see our list of the best dark web sites in 2025. Next, open the Tor browser app and wait for it to connect to the Tor network — this usually takes 5–10 seconds depending on how fast your internet connection is and how overloaded the Tor network is. That said, the Tor browser also has some security issues, so it can’t 100% protect users’ privacy.
Again, we can’t emphasize enough that security and anonymity are paramount to those on dark websites. Obviously, finding these .onion websites is the first challenge, as they won’t show up in Google search results. Dark net websites are called “Tor hidden services“, and they can be distinguished from normal websites by their URLs.
"All of your traffic goes through it, and you have to trust them as if they are your new ISP. Because the backbone of our software is a decentralised network, you don’t have to trust us to browse the internet privately." "If you access 'facebookcore' you are definitely connected to Facebook, because of the nature of Onion addressing — no DNS or Certificate Authority censorship mechanisms are applicable." "If the site invests in setting up a 'native' Tor onion-address for their website, then people who use the Tor browser to access that address never step outside the protection of the Tor cloud," Muffett says.
Free The Internet
Criminals run exit nodes that hijack user traffic for nefarious ends. Keeping restrictions loose ensures the Tor network has sufficient uptime. There’s a big weakness in the Tor network, though. Since no single entity can see all the nodes at once, tracing the actions of any IP address is theoretically impossible. Even fewer know how to access the dark web safely. As a freelance content writer, Stefan can break down complex technological topics, making them easily digestible for the lay audience.
In contrast, the surface web includes public websites that are easily found using search engines. The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. With rising concerns about data privacy, surveillance, and censorship, more people are exploring the dark web to browse anonymously, communicate securely, or access content that might be blocked elsewhere.



