The Safer level enhances security by disabling certain features, and the Safest level entirely blocks scripts, which may impact some functionality. Facebook is aware of attempts by many governments to restrict access to a tool that allows strangers across the web to talk and collaborate freely. Over the last three years, AhMyth is another malicious Android RAT that has been actively traded and discussed on the darknet. Learn how to access the dark web on Android safely with our essential tips and tools for secure browsing. However, internet service providers are unable to decrypt Tor traffic, so they cannot know exactly what you’re doing with Tor.
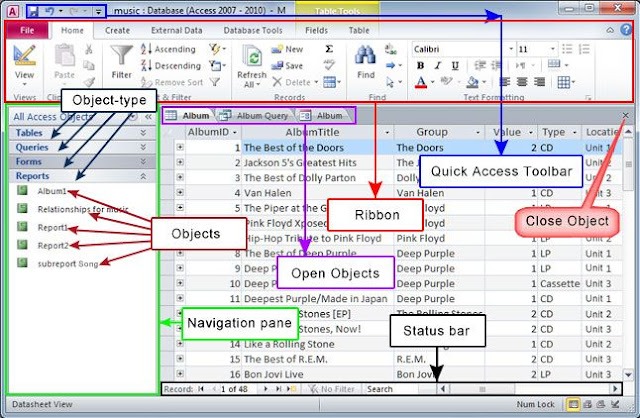
Essential Tools For Accessing Darknet On Android
The Russia-based service accounted for 80% of all darknet market activity and generated $1 billion in revenue annually, TRM Labs says. Secure your data and keep hackers out of your account with a specialized dark web monitoring tool. You must use the Tor Browser or similar applications specifically designed for accessing the Dark Web. The anonymous nature of the dark web also attracts criminals engaged in heinous activities such as distributing child pornography. (Presentation and polish isn’t quite so important on this part of the internet.) Click on any website link, and it’ll appear on screen, with its address at the top.
Where To Find Darknet Market Links Redit
Hackers spend a lot of time on the dark web, and it's not too difficult to get access to hacking tools and data leaks in this part of the internet. With all of that in mind, you need to tread carefully when browsing, in terms of the sites you visit and the other users you interact with. You might often see news stories about criminal activity involving the dark web, and because of what's happening in some corners of the dark web, it tends to put off law-abiding companies and users alike.
How To Access The Dark Web On Phone
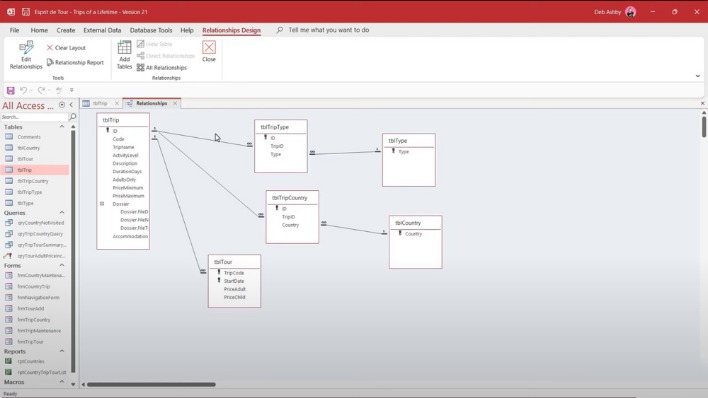
The best and simplest way to safely use the Deep Web on your device is by using the TOR network, which is accessible using specialized apps. That’s why it’s important to use online security tools that protect your personal data. It’s a hidden collective of sites that you could only access through a special browser. Onion sites are used for a variety of purposes, but the common thread is privacy and anonymity, both for users and service providers. While using the Google Play Store version of the Tor Browser reduces risks, the darknet does contain malicious actors.
Any encrypted network unavailable through a search engine and requiring a special software can be considered to be part of the Darknet. The Darknet is an overlay network, which requires special software, tools or configuration to access it. It contains all the well-known websites which can be found through Google or any other search engine. This enables anonymous surfing, combined with access to special .onion sites. The dark web itself isn’t illegal — it’s the sites you visit and what you do that could get you into trouble. These search engines index .onion sites, helping you find the content or services you’re looking for without having to know the exact address.
Which Is Better — Tor Over VPN Or VPN Over Tor?
The darknet is a part of the internet that is intentionally hidden and is inaccessible through standard web browsers. The darknet is a part of the internet that requires specific software and configurations to access. You can then use a Tor-enabled browser, such as Orfox, to access the darknet.Another option for accessing the darknet on your Android device is through Freenet.
Whether you’re using traditional devices or an android phone, the following tips can help secure your online presence and personal information. To protect your data and privacy while navigating these hidden corners of the internet, it’s crucial to adopt specific safety measures. In summary, while some users are motivated by a genuine need for privacy and security, many engage in criminal activities that exploit the unique characteristics of the Darknet.
Weighing Risks Vs Benefits
- Even if you use a secure browser like the Tor browser, you can still be tracked by a search engine like Google that tracks its users.
- However, it does facilitate illegal activities and provides a platform for illicit transactions and services.
- It is a network of websites and online communities that exist outside of the mainstream internet, offering users a higher level of anonymity.
- The Tor Browser is available in the Google Play Store, so getting it up and running to access the dark web is pretty simple.
No, you can access the darknet using standard Android devices as long as you have the necessary applications installed. Yet because it grants anonymity to both website hosts and visitors, it’s also irresistible to criminals who use the dark web as their playground. Keep in mind that many of these sites may contain illegal or explicit content, so proceed with caution and use your best judgment when navigating the darknet.
Risks Of Unofficial Browsers
These search engines can help you discover .onion sites related to your interests. Now that you’re connected to Tor, you’ll need a dark web search engine to help you find .onion sites. This app connects to the Tor network, allowing you to visit .onion sites. By using a VPN and following the tips outlined in this article, you can help to protect your privacy and security while exploring the darknet. It works by routing your internet connection through a series of servers, which makes it difficult for anyone to track your online activity. The Tor browser is a special web browser that allows you to access the darknet.
However, its network is still small, and there aren’t many hidden services available yet. Accessing the darknet on Android offers a gateway to a different realm of information, but it comes with its own set of risks and responsibilities. Keep your device’s operating system and apps up to date, use strong and unique passwords, enable two-factor authentication, and be cautious of app permissions.
Relying on any other browser or unverified application completely negates the security provided by the Tor network. While Whonix is typically run on desktop systems, its principle of forcing all traffic through the Tor network by default highlights the level of security possible. Therefore, layering multiple security precautions is not just recommended; it is essential for maintaining anonymity and safety in these environments.
The darknet is often portrayed as a shadowy realm of the internet, accessible only through specialized tools and software. On one hand, it’s a haven for illegal activities, such as black markets, drug trading, and other forms of illicit trade, thanks to its anonymity. Unlike the surface web, which is indexed by search engines like Google, the dark web requires some digital maneuvering to access its .onion sites. However, while dark web websites need special software to access, that is not the case for deep websites.
It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. It contains many hidden treasures and activities that are not accessible through regular browsers and search engines. When accessing the darknet, security should be your top priority. Below is a detailed guide on how to access darknet android. Before accessing the darknet, it is essential to prepare your Android device properly.
Many people use the Dark Web legally for a range of purposes, from championing free speech to simply wanting to browse the internet with more privacy. And while it’s true that some of this unsavory activity does take place, it’s not the whole picture. Remember, the Dark Web can be a breeding ground for malware; it’s always better to be safe than sorry. All of this information is handled through Google’s own privacy policy, and you are able to delete any info from your monitoring profile or simply stop monitoring completely. The Cerberus RAT is capable of deep surveillance within the victim’s device, interfering with the encrypted communications the phone has with its apps, and outside.
Using an unverified browser can severely weaken the anonymity protections the Tor network is meant to provide. This browser is a specialized version of Firefox that is pre-configured to route your traffic through the Tor network, providing a critical layer of encryption and anonymity by design. Using a standard mobile network or a home Wi-Fi connection to access the Tor network can create correlatable data points for a determined adversary.
Once you have downloaded a Tor browser app, open the app and connect to the Tor network. However, it’s worth noting that using Tor Browser can result in slower browsing speeds compared to using a regular web browser. A VPN’s encryption is particularly key in protecting the connection between your device and the first Tor relay (entry node).
Is It Legal To Access The Darknet?

Accessing darknet services from an Android device carries significant legal and safety risks that must be understood. Finding these .onion sites presents a significant challenge, as there is no centralized or official directory. This process is fundamental for any interaction with .onion sites, which are not indexed by conventional search engines. Accessing the darknet on an Android device requires specific tools designed to protect your anonymity. Exercise extreme caution with every click, as search engines on the darknet are not curated like Google and can lead to harmful or illegal content without warning. These search engines index .onion sites, but their results are often unreliable and can include malicious links.
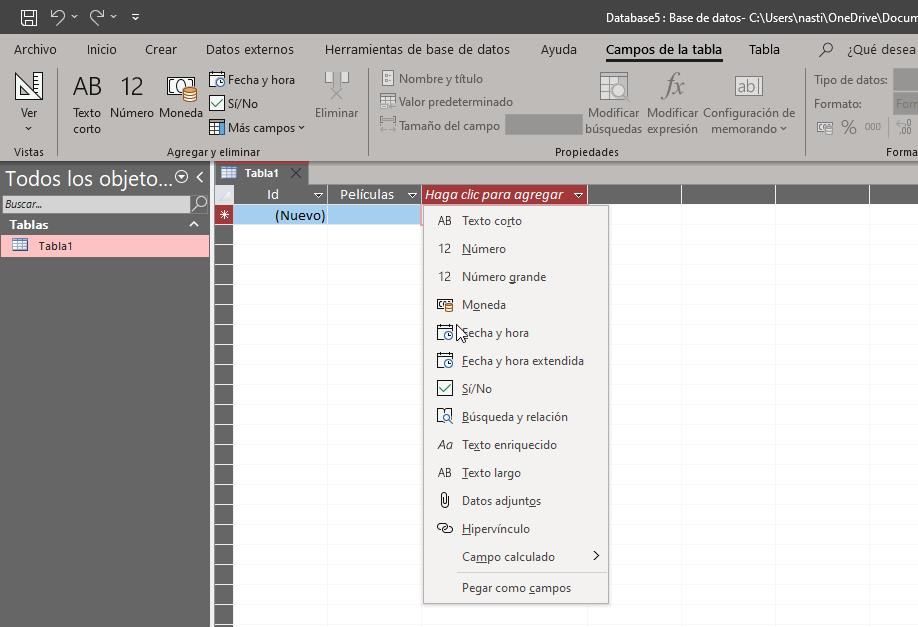
In this case, your traffic goes through Tor’s network first before going through a VPN. Similarly, Data Breach Scanner will monitor all the credentials and credit card details stored in your NordPass vault. It’s essential to research and verify the credibility of a site before visiting. Second, shutting down or controlling access to the dark web would be a huge undertaking and could have unintended consequences.



