
If you’re lucky enough, you can find it on clearnet privacy forums. If you want to find its current links, you can search for terms like “Daniel replacement.” Though it’s still helpful, a static list isn’t enough (we try to keep our own, the one above, up-to-date, though). Hence, you never know when a popular .onion site is going to vanish, or even die.
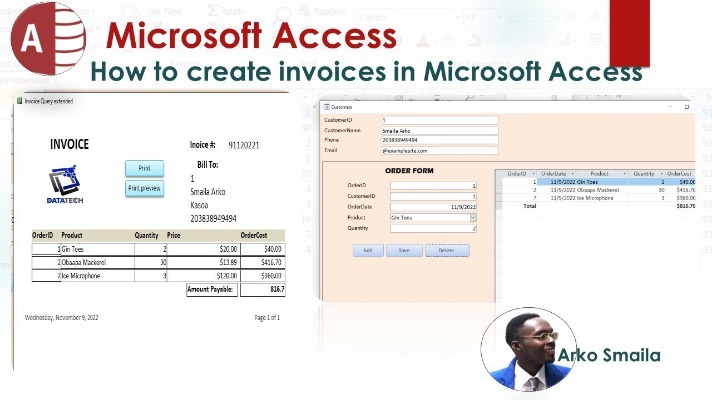
Finding And Accessing Sites On The Dark Web
- Merely downloading, installing and using the Tor Browser is not illegal.
- Not every visitor is a criminal, but this is where most cybercrimes begin.
- Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com.
- You might visit the dark web seeking anonymity or unique services, but this anonymity also attracts scammers.
- With each hop through the network, a layer of encryption is removed, concealing the user’s original location and identity.
Tor Browser already comes with HTTPS-Only mode, NoScript, and other patches to protect your privacy and security. The anonymity that the dark web provides attracts criminals, hackers, and malicious entities. Moreover, the dark web is rife with cybersecurity threats. Engaging with these sites, even inadvertently, can expose individuals to serious legal consequences, including criminal charges. To conduct this check, just turn on your VPN and head over to ipleak.net and dnsleaktest.com to see if the IP address displayed is the one from your VPN.
Best Practices For Accessing The Dark Web
We’ll focus on secure, ethical practices tailored to cybersecurity professionals and IT leaders. In this guide, we’ll cover the dark web access guide, explain how to use Tor browser safely, and answer key questions like is it safe to browse the dark web. Additionally, if Tor leaks, your IP address will be exposed to everyone.
What Is The Role Of Relays In Tor?
The deep web makes up approximately 90-91% of the internet. The deep web is in between the surface web and the dark web, and it constitutes the large majority of the actual internet. Although the surface web only comprises about 4-5% of the entire internet, scope is important to keep in mind because this is still impressively expansive. The surface web is what the average daily internet user interacts with the most. Cybercrime is getting more sophisticated, putting businesses at a serious disadvantage when it comes to protecting their networks.
The dark web isn’t off-limits, but it’s not built for casual browsing. Freenet is great if you want to publish or retrieve content without censorship, but not for interactive browsing. These freesites are static pages you can visit anonymously once Freenet loads in your browser.
Tor’s anonymity function is used by everyone from human rights workers and journalists through to drug and arms dealers. This makes it very difficult to trace the original users’ identity. The browser is open-source software that is free to download and enables anonymous communication online. Whether your search engine of choice is Google, Bing, Baidu, Yahoo!
Step 3: Adopt “operational Security”
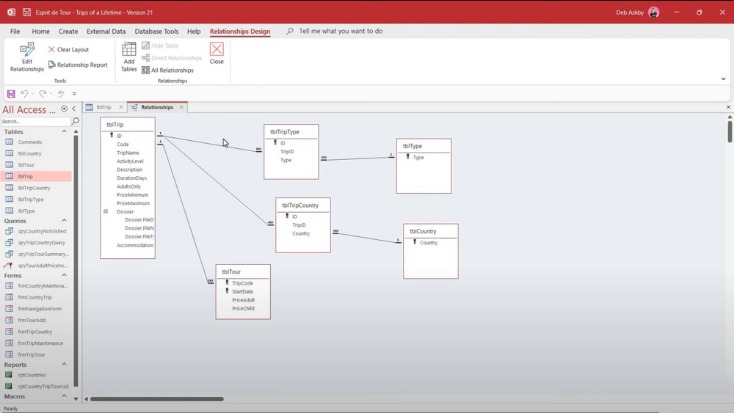
For this reason, you cannot browse through these sites using your default search engine. This way, you can protect yourself from websites that want to steal your login details or cryptocurrency. These search engines work best if you already know what site you’re looking for, not for general browsing.
Can Tor Browser Be Used For Regular Internet Browsing?
These include the sale of drugs, weapons, counterfeit documents, stolen data, and illegal pornography. While it enables privacy for legitimate activities such as whistleblowing, political dissent, or private communications, it is also used for illegal operations. Users rely on directories, forums, and invite-only platforms to find addresses. Accessing the dark web also requires knowledge of where to go, since search engines like Google do not index these sites.
Limit Tracking On The Tor Browser
Here’s how to stay safe while accessing the dark web. However, note that dark web search engines don’t index as many sites as regular search engines, so results can sometimes be limited or outdated. To ensure your traffic is properly routed through the Tor network, you’ll also need to install Orbot, which helps secure and anonymize your connection. The Tor Browser is available in the Google Play Store, so getting it up and running to access the dark web is pretty simple.
If you'd still like to visit onion sites and see what the other side of the internet has to offer, there are alternative ways you can try. When you browse with Tor, websites and observers will see the IP address of the Tor "exit node" (the final relay in the chain), not your own. Imperva DSF flexible architecture supports a wide range of data repositories and clouds, ensuring security controls and policies are applied consistently everywhere. While risky and requiring strict operational security, cyber HUMINT gives defenders access to information not available through passive monitoring alone.
If you need academic journals, check out our article on using deep web search engines for academic and scholarly research. These are okay, but specialized search engines are better than general ones for finding info on the deep web. Many of the best general deep web search engines, like Alltheweb, DeeperWeb, and CompletePlanet, have shut down or been acquired. Much of it is tucked away in databases that Google is either uninterested in or barred from crawling.
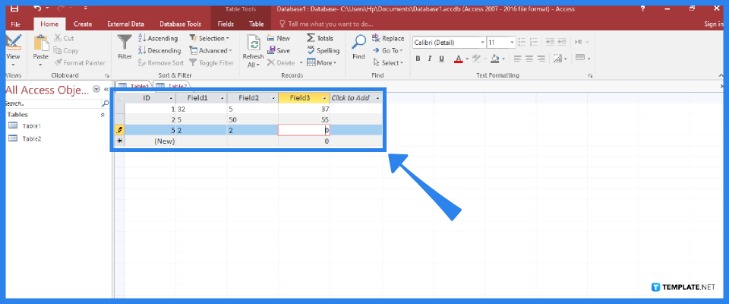
Dark Web Search Engines
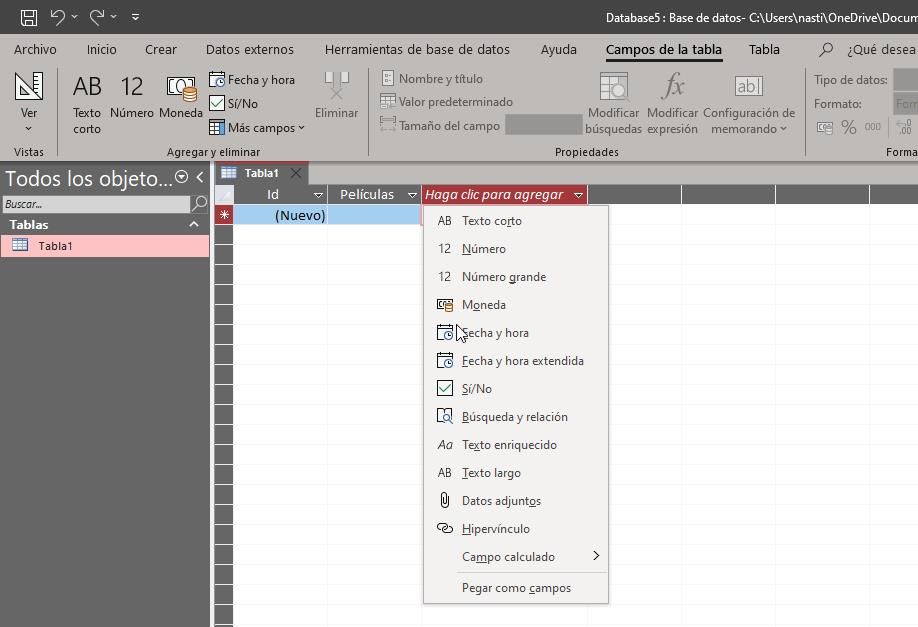
Only visit trusted websites with URLs that are maintained by a trusted source. All v3 .onion addresses (the current standard) are 56 characters long and end with “d” to denote the URL version in use. To do so, enter a .onion URL and you’ll be taken to the dark web page being served at that address. While it’s generally safe to use, dark web activity can be detected at the entry and exit nodes of the Tor network. So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations.

For built-in Tor over VPN functionality, NordVPN operates specialized servers that automatically route you through the Tor network. If you connect to your VPN and fire up Tor Browser, you’re using Tor over VPN. While somewhat similar, Tor emphasizes anonymity, and a VPN emphasizes privacy. The more specific you can be, the better, or else you’ll end up with the same search results you would find on Google.
This node decrypts your traffic, and it reaches the destination, i.e,. It works by routing your traffic through multiple nodes. While the Tor Browser is great and safe, it’s not as great as another component – a VPN. Compare this to getting on the dark web and the way that part of the internet works.

Can I Access The Dark Web Without Tor On My Phone?
Each server our request passed through had a distinct IP address. Whenever you visit any website, click the circuit button next to the domain to open a menu displaying the servers through which your traffic passes. However, seeing is believing, and the Tor browser allows you to see which servers your traffic passes through. We’ve talked about the Tor protocol bouncing your traffic through multiple remote servers. Hence, you’ll see accurate search results similar to searching on Google. DuckDuckGo uses its web crawler and also curates data from over 400+ sources, including Google and Bing.
The dark web marketplaces thrive on the demand for illegal services and extreme content. Law enforcement agencies in many countries monitor the dark web to combat illegal activities. Your access to illegal content, even if it is unintentional, can violate laws in many countries.



