Privacy tools and services, like anonymous email platforms and virtual private networks (VPNs), contribute to the Dark Web’s reputation as a refuge for those prioritizing online anonymity. Cybercrime services, such as hacking tools and stolen databases, are available for hire, creating a marketplace for illicit online activities. Over the years, the Dark Web has gained a certain level of notoriety due to its association with illegal activities, including the trade of illicit goods, hacking services, and various forms of cybercrime.
However, understanding how it works is crucial for appreciating the broader landscape of online privacy and security. This includes implementing multi-factor authentication (MFA), using robust firewalls, regularly patching systems, and encrypting sensitive data. Specialized threat intelligence services can scan dark web forums and marketplaces for mentions of your company’s data. Companies should actively monitor the dark web for stolen employee credentials, customer data, and intellectual property. A VPN encrypts your traffic and routes it through one of its own servers before it enters the Tor network. While Tor provides anonymity, it doesn’t hide the fact that you’re using Tor.

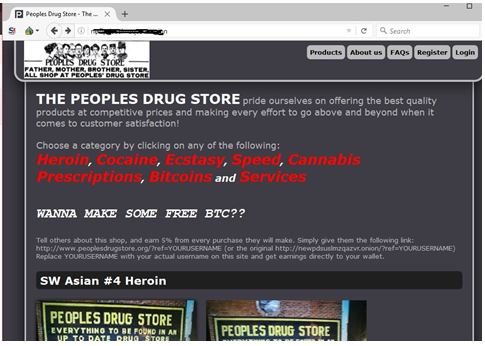
Drug Trafficking Sites
It works well, it’s free, and it provides decent privacy since it’s open-source. That’s why I recommend using a VPN before you access Tor, as it will prevent any Tor server from seeing your real IP address. Yes, but only from the sites you connect to — instead of your IP address, they will only see the IP address of a Tor server. What’s more, it’s also hard to establish a VPN over Tor connection, as most VPN providers don’t support them. And anyone (including your ISP) can see that you’re connected to Tor.

Remember only to make purchases using digital currencies and never provide any online banking login details. If you plan to purchase on a dark net marketplace or dark web commerce sites, you’ll need to create a fake identity. Reddit is also a valuable resource for finding the dark net or deep website you’re looking for. The dark web has no shortage of criminal activity, scams, phishing sites, suspicious links, and malware designed to trick newbies.

Robotsnet Uses Cookies To Improve Your Experience And To Show You Personalized Ads Privacy Policy

Unlike the public web, it can’t be accessed through standard tools like Google, Firefox, or Chrome. Cryptocurrency is often used for payments on the dark web, exposing users to fraud or money laundering schemes. Many dark web marketplaces are scams designed to exploit unsuspecting users. For example, data breaches frequently result in stolen information being sold on the dark web. Whether you’re for or against using the dark web, it helps to know what it is and how to navigate it. Rather than weeding out the genuine web users from the criminals, many website owners find it easier just to block all Tor users.
Be Cautious With Downloads
All applications are automatically blocked if they try to access the internet without using Tor, Persistent Storage is encrypted by default, and as mentioned above, nothing is ever written to the computer’s hard drive. This includes evidence of any websites you visit, files you open, passwords you use, and even any other devices or networks you connect to. Government cyber teams can take such websites down, arrest the owners and then use the website to track and follow users that show activity on the website. In addition to the brief introduction of “fake” marketplaces on the dark web, dark web users visiting political sites on the Tor network should realize that government-funded cyber teams are on the lookout for such users. This enables individuals to form groups and only share content in a highly anonymous network of darknet users who they know. Additionally, I2P doesn’t rely on hidden directories that serve as a resource for .onion domains.
Step 4: Boot Into Tails OS From The USB Drive
When you go on the dark web and visit the site, your traffic is decrypted, and everything functions the same. You get one encryption layer from a VPN, and when you’re in Tor, you get another layer. Some countries frown upon dark web usage, so it’s good to cover your back with a reputable VPN service. A VPN is a confusing factor for many because there are two ways to use it with Tor.
Navigating With Dark Web Search Engines
Clicking on links there might take you to illegal or harmful material without warning. The dark web is full of unknown and potentially dangerous content. Security solutions like anti-virus software protect your system and network from malware and other threats. You should review access to your camera, location, and microphone regularly to ensure no website has unnecessary permissions. What’s more, they can also sell you personal information on the dark web as your personal data has a monetary value on the dark web. Then, they can use your data to impersonate you and run social engineering attacks to target your loved ones.
Tor-over-VPN Vs VPN-over-Tor: The Right Order
The surface web is the open part of the internet, which includes publicly accessible websites and resources. In contrast, the surface web includes public websites that are easily found using search engines. The dark web is a hidden part of the web that is not indexed by traditional search engines like Google and requires specialized software to access. Instead of search engines, you’ll need to rely on directories or specific .onion links.
Tor blocks JavaScript by default, but this addon lets you permit it for trusted sites. This addon allows you to control which sites can executive JavaScript and which ones can’t. We’ve explained how Tor protects your privacy by routing traffic through multiple servers. Regular browsers can’t open Onion sites because they aren’t part of the standard domain name system. The above configurations help improve your security when surfing the web via Tor. This feature can’t be changed because it’s integral to Tor’s privacy focus.
- Accessing the dark web is legal, but engaging in or supporting illegal activities while there is not.
- Journalist in India → Uses Tor to access a whistleblowing portal → Submits information anonymously while protecting their identity.
- It’s a segment of the internet hidden from view, not showing up in search results or accessible through regular web browsers.
- ExpressVPN is an excellent choice for Tor and accessing the Dark Web.
While Tor browsers are used to access the dark web, search engines play a crucial role in facilitating the browsing experience for users. These networks each operate differently but share the goal of protecting anonymity and providing access to unindexed online spaces. The deep web consists of unindexed content not accessible via standard search engines. This is the publicly accessible portion of the internet that can be indexed by search engines. It’s also best to only use trusted directories or search engines that show safe links, like Not Evil, to reduce your risk of ending up on fake, malicious sites.
Critical Security Settings
The Tor Browser is a popular online anonymity tool among political activists and journalists who fear totalitarian governments monitoring or arresting them. You can access these websites without worrying about someone snooping on a Tor exit node, offering more private browsing of what is known as the deep web. The Tor Browser (“The Onion Router”) is a product of the Tor Project, which was founded on the belief that “internet users should have private access to an uncensored web.” If you are reading this, you’ve likely heard about how the Tor Browser can help protect your internet privacy and anonymity online. Initially designed for secure military communications, it evolved into a broader tool for online anonymity, later expanding to public use with the Tor network.
Connecting To The Tor Network
A specialized search tool for researchers focusing on darknet marketplaces (use with extreme caution). Offers an extensive archive of dark web sites, with both free and premium versions. Consider using a separate laptop or virtual machine solely for dark web access to reduce the risk of malware infection on your primary system.
Downloading and installing the Tor Browser is the first step towards accessing the Dark Web securely. The Tor Browser is the most commonly used software for accessing the Dark Web. Using a VPN in conjunction with the Tor Browser adds an extra layer of security and anonymity. A Virtual Private Network (VPN) is a service that protects your internet connection by encrypting your data and routing it through a remote server.



