
If you lived in these four states during the breach period, you automatically qualify for a statutory payment of approximately $100—no proof of damages required. This makes genetic data breaches uniquely damaging and long-lasting. Unlike a direct system breach, these criminals exploited customers who reused passwords across multiple sites. Your name, ancestry data, genetic matches, and even health information may have been exposed.

The dark web exists within the deep web and holds content that is accessible only using the Tor network. They help users find real dark web links, verify them through uptime tracking, and avoid dangerous clones. Cross-check onion links with trusted directories like dark.fail or onion.live, and never follow a link blindly. Some are created purely to trick users into clicking harmful or phishing links under the illusion of legitimacy. OnionShare lets users share files directly from their device over a temporary .onion address without needing a centralized server.

The market is also known for its listings related to financial fraud, such as phishing tools and stolen credit card information. It offers a wide range of illicit goods, including illegal drugs, counterfeit items, fake IDs, passports, and software keys. Dark web markets have gained notoriety for their illicit offerings. Transactions are made using cryptocurrencies to maintain anonymity. Are you struggling to stay on top of the main dark web markets worth monitoring?
Mistake #1: Choosing Markets Based Only On Size
This platform, accessible via the Tor network, offers invaluable resources, legal advice, and support for individuals seeking to unveil wrongdoings. The platform’s commitment to user privacy is evident in its robust encryption protocols and its stance against data logging. Whether users are seeking specific information, resources, or merely exploring out of curiosity, Ahmia delivers comprehensive and relevant search results. Its intuitive interface, combined with advanced security features, ensures that users can manage their cryptocurrencies with confidence. Prioritizing user privacy, it offers coin mixing services to ensure the anonymity of Bitcoin transactions. This platform provides a sanctuary for users to connect, share insights, and engage in discussions without the constraints of mainstream platforms.
- The dark web operates on “darknets,” which are overlay networks that run on top of the regular internet.
- These services are used to obfuscate the origins of cryptocurrency transactions, making it harder to trace them.
- Many of them are safe for beginners to use since they filter out dangerous/illegal content to only provide safe .onion links.
- The magic behind the dark web’s anonymity is a process called onion routing.
- The categories are well organized, ranging from drugs and fraud to digital products, guides, and malware.What really sets it apart is its focus on security and usability.
- What sets it apart is that it doesn’t track your searches or create user profiles, making it ideal for anonymous browsing.
News And Media Platforms
Riseup is a dark web platform that offers secure messaging solutions. Proton also offers other security tools besides ProtonMail, such as Proton Drive, Proton Pass, Proton Calendar, and Proton VPN. The platform utilizes end-to-end encryption, ensuring it does not store any activity records.
The deep web is the part of the internet you can’t access through search engines like Google and Bing. The encryption technology routes users’ data through a large number of intermediate servers, which protects the users’ identity and guarantees anonymity. Haystak also offers a premium version that allows advanced search, access to historical content, and email alerts. Founded by security researcher Juha Nurmi, Ahmia is essentially a list of “hidden” sites that do want to be found. By prioritizing security at every level of its service, Impreza Hosting provides a secure foundation for websites, ensuring that they are resilient against various cyber threats and surveillance efforts.
Privacy Essentials: Metadata Editor And Remover Tools
That’s why we took the guessing work out of it for you, and made this list of the best dark web sites you should check out. The dark web remains a largely unregulated and unmonitored part of our digital world. However, some significant security risks still remain because the dark web is not regulated. Ahmia, for example, filters its results to block illicit or harmful content. While no search engine is entirely without risk, some are designed with safety in mind.
Monthly Customer Engagement Report For Websites
The Torch platform is among the most popular and long-standing dark web search engines, raking in over 80,000 daily search requests. With its nifty “conjoin” feature, users can combine different coins in one transaction, covering the user’s tracks and maintaining their anonymity. It’s for the good that these sites are not available for the general internet user. Ahmia is a safe alternative search engine for users who prefer the dark web.
Pro Tip: Use A VPN To Stay Safe On Onion Websites
Also, people share reputable dark web links on encrypted apps like Telegram or Keybase. However, you need a working link to access it, which you can find on the clearnet privacy forums if you are lucky. To find its current versions, search for terms like ‘Daniel replacement’. The best approach is to learn how to find new and active links yourself. The operating system is ideal for journalists, activists, and researchers who need system-level protection beyond a standard browser.
Top 10 Dark Web Search Engines Of 2026 For Safe & Private Access
The vast expanse of the internet is like an iceberg, with a significant portion of it hidden beneath the surface. If you are concerned with staying on the right side of the law with your use of onion sites, stick to exploring only the verified lists of onion sites, educational resources, or privacy-oriented resources. There certainly are dark web markets, or other illegal platforms, in this space. The Tor network itself was designed originally for secure communications by the government, and is used frequently by journalists, human rights activists, and privacy advocates. As technology changes, so has the Tor network, which has moved from anonymity to a potent marker of digital independence.
Secure Communication And Collaboration Tools
- Always run the latest version of the Tor Browser to protect against security vulnerabilities.
- However, you can find legitimate content and activities here, too.
- While not technically a dark web exclusive site, Sci-Hub is repository offering free access to millions of research papers and articles, bypassing traditional paywalls.
- The deep web is always changing, influencing people’s access to knowledge, privacy protection, and secure communication.
- Tails is a unique operating system tailored for those who prioritize privacy and security.
Though people usually think of dark websites as the wrong online place, that’s not the complete truth. You can use HTML templates and follow guides on how to host an onion with tools like Tor + Tails. These are some of the best deepweb sites 2026, offering both utility and anonymity. Before you upload, clean every file with a metadata editor and remover. Use Tails or Whonix—both are secure operating systems designed for anonymity. If you’re looking to host an onion site or send private documents, using a metadata scrubber is as important as encryption.
Despite the predominance of illicit activities, Dread also hosts conversations related to privacy and cybersecurity, reflecting the diverse range of topics covered on dark web forums. After the shutdown of RaidForums, BreachForums filled the gap by hosting discussions on exploits, data leaks, and cybercrime. Launched in March 2022 as a successor to RaidForums, BreachForums quickly became one of the leading forums for discussing data breaches and sharing stolen information. It is heavily business-oriented, with sections dedicated to ransomware services and cyberattacks. Initially known as DaMaGeLaB, the forum rebranded in 2018 after the arrest of one of its administrators. Some are geared towards academic, professional, or hobbyist communities, while others are havens for illegal activities.
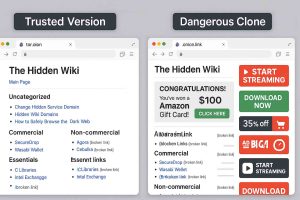
For example, the Silk Road site operator, an illegal dark web marketplace, was traced and arrested. Moreover, malicious actors can attempt phishing scams to steal your data and identity for extortion. Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.
In recent years, law enforcement has shut down services like Smartmixer and is now intensively pressuring the remaining operations. While Tor hides your IP and location, mistakes like revealing your personal information, using unsafe links, or running scripts can expose your identity. To stay safe, use trusted links and avoid sharing your personal information. Nonetheless, don’t assume that the dark web will hide your illegal actions – you will still get caught.
The system is designed to provide enhanced security and privacy features. Furthermore, it’s critical to understand that Whonix is not a stand-alone browser. It can only interact with the gateway, the most effective method by which the browser protects user applications from learning a device’s IP address. While accessing the dark web using Mozilla Firefox is possible, you must first adjust its settings. The Invisible Internet Project’s distinctive feature is its ability to use decentralized file storage with the help of the Tahoe-LAFS plugin. I2P, or the Invisible Internet Project, allows you to access the ordinary and dark web.
The platform has been an invaluable resource for data and analytics, offering detailed insights into blockchain activity, including transaction volumes, wallet activity, and network health. This wallet service emphasizes security and privacy, with advanced measures in place to protect users' funds while providing them with full control over their private keys. The platform started primarily as a blockchain explorer, allowing users to view and analyze transactions on the Bitcoin blockchain in real-time. Since its inception in 2011, Blockchain.com has played a crucial role in the adoption and understanding of Bitcoin and other cryptocurrencies by providing an accessible and user-friendly interface for users to manage their digital assets.
If new platforms come up, the control of this area would be lessened by the existence of special search tools which are geared towards hidden networks. This area has turned to be a dependent source for years of journalists, researchers, and privacy-centric users who trust on anonymous networks like Tor and the principle of onion routing. The dark web and deep web are home to countless hidden forums where users discuss everything from privacy tools to cybersecurity to hacking,… Essentially, any content behind a login or stored in a private database is in the deep web, which makes up roughly 90% of all websites. Blockchain.info’s onion site allows users to manage Bitcoin wallets and view blockchain data securely. Torch is a trustworthy dark web search engine that allows users to find onion sites easily.



